
Главная страница Случайная страница
Разделы сайта
АвтомобилиАстрономияБиологияГеографияДом и садДругие языкиДругоеИнформатикаИсторияКультураЛитератураЛогикаМатематикаМедицинаМеталлургияМеханикаОбразованиеОхрана трудаПедагогикаПолитикаПравоПсихологияРелигияРиторикаСоциологияСпортСтроительствоТехнологияТуризмФизикаФилософияФинансыХимияЧерчениеЭкологияЭкономикаЭлектроника
Cyber Crime Investigator
|
|
 When a cyber crime is committed, there are many methods of investigating every detail of that crime. One is to check the cell phone records, email records, computer files, etc. This is called computer forensics – " the discovery, analysis, and reconstruction of evidence extracted from or contained in a computer, computer network, computer media or peripheral."
When a cyber crime is committed, there are many methods of investigating every detail of that crime. One is to check the cell phone records, email records, computer files, etc. This is called computer forensics – " the discovery, analysis, and reconstruction of evidence extracted from or contained in a computer, computer network, computer media or peripheral."
This includes password protected information, tracing the source of e-mail, recovering deleted data, restoring instant messages, remotely monitoring computers and preserving digital evidence for presentation in court.
Examining a computer to discover what data is stored on it is a time consuming and painstaking process. There are various types and amounts of information in a computer that are considered valuable from the evidence point of view. All of these files must be retrieved: deleted files, documents, images, and password protected information and hidden files.
The demand for forensic computer support is growing logarithmically. The investigation of even routine cybercrimes requires skilled specialists. They must be able to track email accounts, analyze email headers, expertise in cyber forensics, recover evidence from encrypted files, password protected files, analyze log files. Criminals learn the technology and are taught by other cyber criminals. That is why ability to extract that information and present it reliably in court is one of the most rapidly increasing demands in the area of computer technology.
The missions of special computer crime task forces are 1) to stop the spread of malicious code; 2) to identify and thwart persons who use the Internet to meet and exploit children; 3) to counteract operations that target intellectual property, or national security; 4) to dismantle criminal enterprises engaging in Internet fraud. 
Here is an example of cyber crime investigators’ work:
The Turkish and Moroccan hackers released a computer worm into cyber space to steal credit card numbers from thousands of infected computers around the globe.
But the “Zotob” malicious code caused computer systems crash and spontaneously reboot. That got the attention of the FBI. They forensically analyzed the computer code for identifying its possible authors. In no time, investigators traced the worm to Turkey and Morocco. Authorities there agreed to help.
Small, highly trained team of FBI agents, analysts, computer forensics and malicious code experts shared with Turkish and Moroccan authorities the information they had gathered — including IP addresses, e-mail addresses, names linked to those addresses, hacker nicknames, and other clues uncovered in the computer code.
Local law enforcement analyzed and acted on that information, arresting two suspected Zotob perpetrators less than eight days after the malicious code hit the Internet. Computer forensic experts verified that the code found on seized computers matched what was released into cyberspace.
I. Translate the following words:
1) to commit [ 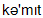 ] 2) court [
] 2) court [ 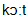 ] 3) painstaking [
] 3) painstaking [  ]
]
4) evidence[ 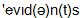 ] 5) to thwart [
] 5) to thwart [ 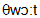 ] 6) to dismantle [
] 6) to dismantle [ 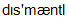 ] 7) clue [
] 7) clue [ 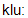 ] 8) to suspect [
] 8) to suspect [ 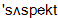 ] 9) perpetrator [
] 9) perpetrator [ 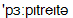 ].
].
II. Translate the word combinations and find them in the text:
1) преступление в сфере информационных технологий 2) судебная экспертиза 3) информация, защищенная паролем 4) удаленные файлы 5) скрытые файлы ● 1) злочин у сфері інформаційних технологій 2) судова експертиза 3) інформація, захищена паролем 4) видалені файли 5) приховані файли
На латинице.
III. Make ten questions of different types to the text.
IV. Make a detailed plan for the retelling of the text.
V Give the full name of the shortenings and explain the meaning:
FBI; CIA
|
|