
Главная страница Случайная страница
Разделы сайта
АвтомобилиАстрономияБиологияГеографияДом и садДругие языкиДругоеИнформатикаИсторияКультураЛитератураЛогикаМатематикаМедицинаМеталлургияМеханикаОбразованиеОхрана трудаПедагогикаПолитикаПравоПсихологияРелигияРиторикаСоциологияСпортСтроительствоТехнологияТуризмФизикаФилософияФинансыХимияЧерчениеЭкологияЭкономикаЭлектроника
Calculation of costs of operation and maintenance of the equipment
|
|
2.5 Calculating the cost of electricity is calculated as follow formula (2.1):
СE=Pe*SPi*ni*Tpi (2.1)
where:
Pi – Power of i - th type of equipment, W;
Tpi – Time while the i-th type of equipment, hour;
ni – number of units of the i-th equipment;
Pe – the price of one kilowatt-hour of electricity (15.19 KZT/kWh).
Substituting into the formula (4.4.3) we get:
CE=15.19/1000*(150+150)*352
CE = 1604, 064 KZT.
The electricity cost is shown in Table 2.4
Table 2.4 – Electricity costs
| № | Name of equipment | The number of pieces of equipment, pcs | Power of equipment, W. | Working hours, hours | Cost of electricity, KZT |
| Dell Inspiration 2350 | 802, 032 | ||||
| Oculus Rift | 802, 032 | ||||
| Total: | 1604, 064 |
The items, included to the estimated total costs of the work are summarized in Table 4.5:
Table 4.5 – Estimated cost
| № | Cost items | Sum, KZT |
| Materials cost | 735 176 | |
| Cost of maintenance and operation of the equipment | 1 604, 064 | |
| The basic wage | 360 000 | |
| Additional wage | 72 000 | |
| Charges to social security payroll1 | 36 000 | |
| Total: | 1 204 780, 064 |
3. DEVELOPMENT OF OWN CREATION PROGRAM DATABASE EPIZOOTIC SITUATION ONTHE HELMINTHIASES ON AGRICULTURAL ANIMALS IN SOUTHERN KAZAKHSTAN
Let’s show you some of my cases.
3.1 Structural parts developed database:
DB consists of 6 and Tables:
- table area which th placed data in accordance with nature one – comzones am;
-Table areas;
-Table districts that houses the data type of the studied animals and their ages;
-Table parasites, which placed the number of animals tested data, the species name of the parasite, intensity, extensiveness of infected animals and the date of the investigations;
-Table species;
-Table types of parasites
Table areas consisting of three fields. This field of natural and ecological zones, regions and field names automatically uelichivayuscheesya field. Natural and ecological zones were not fixed output in a separate table, because one does not have to oblat takuzh and a lot of natural and ecological zones.
Next comes the table of areas in which there are three fields. The first field - this automatically increasing the growth rate, the second a field of corresponding areas of the field increment table. It is for this field relate the two tables. For example, when you select an entry in the table of areas there is a situation in kotoryi of the selected entry is taken inrkementa value and compared with a value of areas of the table. If there are such items in the table areas, such records are displayed. So obrahom carried irerarhicheskoe interaction between all database tables.The table areas there is a field with the name of the district.
Table county has 5 fields. This field avoinkrementa, the whole field corresponding autoincrement table areas, field names orkruga, the whole field is the name of the animal species. This field yavlyatsya whole of practical purposes. This issue will be discussed in more detail below. At this point, it suffices to know that the floor w corresponding increment of the other table names of animals. Since the names of the animals is sufficiently small, and they are introduced on a regular basis in the processes of introducing a new record, it was appropriate to make such a logical move, as the imposition of animals.Name of authorized types of data in a separate table. When you add a new entry in the table of counties a drop-down list from which you can choose the type of animal neohodimo for this entry. In the table of animal species there are only two fields - a field auto-increment field and the name of the animal. The drop-down table spiork districts formiruestya just from the table of animal species, but this list is not displayed avtoinrkementa field. When you select an entry from the list in the table field names orkugov animal entered an integer corresponding to the increment of the number of separate table Vido, opposite which is a necessary and text titles that the user sees the program. All this technology is hidden from the user.
For added convenience, and the names of species of parasites have been ruled enes from the main table in the main table were only numerical key values on which they are determined DATA E fields from the secondary table. This is done so that the user program to enter data such as the type of animal, once a secondary table, and later when you add a new post, he could choose the right kind of animal from the dropdown list. Same thing with the name of the parasite. Any transactions in these tables can be made in a separate window by selecting the line " Animals" section of the menu, or " names of parasites."
Editing parasites in separate meters of KNE (Fig.3.1):
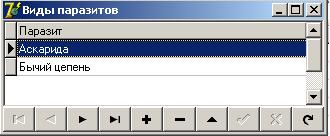
Figure 3.1 - Editing parasites
Each table has a unique numeric identifier that table connected to each other. They are permanent it is invoked when editing, adding and deleting records and hierarchical dependecies. Also it is necessary in the construction of various queries.
3.2 The main edit window
Editing table was delivered Eno in a separate modal window. This modal window has four areas of editing. This is great for adding and editing data. You can add or find necessary data without using special requests, and in a very short time. Each region is located on the database hierarchy, from left to right and top to bottom. At the bottom there are four buttons for editing, adding and deleting of data. In the program, these functions were not provided by the language the SQL, they are made by standard procedures, the Delphi, which are available in these display components.
In the editing process provided by the emergence of some common mistakes. For example, the user is immune from the introduction of new data, inappropriate hierarchy table. This is done as a means of the Access, and directly to the environment the Delphi. You will not be able to carry out the removal of the same data, if the lower hierarchy are entries related to the data (Fig. 3.2).

Figure 3.2 - The main window for editing
For greater clarity, this form has been divided into four parts according to the appropriate editing tables. When you select any field of any table automatically displays the child tables in other forms of editing. For example if you select the first form Zhmbylskuyu region, the second form will automatically appear relevant İ nö nü districts of Zhambyl region, further otobrazatsya District corresponding to the first in the list of the area belonging to the selected area. Further displays all districts, and then in the hierarchy, respectively, form the parasite takes a logical view.
After the required action on the data, the user can close the edit box and immediately move to the main window of the second program.After the transition is necessary to press the refresh button to display the new data. Here d and nnye on all four tables are arranged in one and displayed in accordance with the hierarchy in alphabetical order. In this window IME e tsya 11 entry forms to create unique queries to our data. For example, in the input box on the query area is enough to enter the letter " M" to bring all areas starting with that letter. This is very useful when the user is inconvenient to enter full name required. Similarly all input fields allow for entries in other input forms. Due to this feature, you can create unique demands, satisfying the requirements of the user. After completion of the necessary operations, you can press the refresh button, and then take shape our original form and all requests zeroed.
These can and designed to provide the most user-friendly interface between the operator and the program. The windows are well manifested the hierarchy of the database itself from right to left and top to bottom. You can quickly find the necessary data and edit them. To prevent any violations of the hierarchy, it is provided by means of the MS the ACCESS.
Code implementation of editing:
procedure TForm6.DBGrid1Exit (Sender: TObject);
begin
try
if datamodule2.ADOTable1.Modified then
the dat amodule2.ADOTable1.Post;
except
end;
end;
procedure TForm6.DBGrid2Exit (Sender: TObject);
begin
if datamodule2.ADOTable2.Modified then
datamodule2.ADOTable2.Post;
end;
procedure TForm6.DBGrid3Exit (Sender: TObject);
begin
try
if datamodule2.ADOTable3.Modified then
datamodule2.ADOTable3.Post;
except
datamodule2.ADOTable3.CancelUpdates;
datamodule2.ADOTable3.Cancel;
end;
Figure 8. Heads n th window.
Request code:
datamodule2.ADOQuery1.Active: =false;
datamodule2.ADOQuery1.sql.Clear;
datamodule2.ADOQuery1.sql.add ('SELECT *');
datamodule2.ADOQuery1.sql.add('FROM Areas, Regions, Districts, Parasites ');
datamodule2.ADOQuery1.sql.add ('where (keyparazit = key11) and (keyokrug = key1) and (keyrayon = key)' +
'AND Natural _ zone LIKE (' '' + edit10.Text + '%' ') AND FIELD LIKE (' '' + edit1.Text + '%' ') AND' + Neighborhood LIKE ('' '+ edit2.Text + '% '') A the ND District LIKE ('' '+ edit3.Text + '% '') ');
if (dblookupcombobox3.KeyValue> = 0) then
datamodule2.ADOQuery1.sql.add ('and (Vidzivotnogo =' + inttostr (dblookupcombobox3.KeyValue) + ')');
datamodule2.ADOQuery1.sql.add ('and (Vozrastzivotnogo LIKE' '%' + edit13.Text + '%' ')');
the dat amodule2.ADOQuery1.sql.add ('and (Kolvo the BETWEEN' edit4.Text + + 'the AND' edit5.Text + + ')');
if (dblookupcombobox2.KeyValue> = 0) then
datamodule2.ADOQuery1.sql.add ('and (Parasite =' + inttostr (dblookupcombobox2.KeyValue) + ')');
datamodule2.ADOQuery1.sql.add ('and (procent the BETWEEN' edit7.Text + + 'the AND' edit8.Text + + ')');
datamodule2.ADOQuery1.sql.add ('and (Density BETWEEN' + edit6.Text + 'AND' + edit12.Text + ')');
s2: = Copy (edit11.Text, 0, 3);
s1: = Copy (edit11.Text, 4, 3);
s3: = Copy (edit11.Text, 7, 4);
s4: = s1 + s2 + s3;
datamodule2.ADOQuer y1.sql.add ('and ([a Date] < = #' + s4 + '#)');
s2: = Copy (edit9.Text, 0, 3);
s1: = Copy (edit9.Text, 4, 3);
s3: = Copy (edit9.Text, 7, 4);
s4: = s1 + s2 + s3;
datamodule2.ADOQuery1.sql.add ('and ([Date]> = #' + s4 + '#)');
datamodule2.ADOQuery1.sql.add ('ORDER BY Natural _ zone, state, district, type of animal, age of animal, parasite, percent, age, sum, date; ');
datamodule2.ADOQuery1.Active: =true;
In the upper area there are components that are familiar to us code the SQL - query. In the event the function of each component included the SQL - query code which is repeated every time when a corresponding event, such as changes in the input line area.
By changing the text in the various components can achieve a unique request, satisfying all the records of all database tables.
Also in the main window, there are the lookup - field. In these fields from the drop down list to select the point on which the later will link be sorted. That point may yavlyatsya name of the parasite or the type of animal. The source of these data fields are separate tables in the database. In these tables, there are only two fields: field of the form and its Idex, which grow automatically as you add new database entries sredstvmi the Access. Posel choice please click on the button located on the lookup - component. In response button is the possibility of determining a species and its index, which were later recorded in the component ADOQuery. This method is widely applied in all bases.This is very handy when there is a certain limited set of records, which is to enter each time anew is not the best solution. It is much easier to bring such elements in a separate table by assigning them a certain automatically-growing index. In the main table, you can make only the number indesksa and the mapping database table to replace the index corresponding elent of the secondary table. Thus, solved several problems:
-without mistakes
-speed of filling
-saving disk space
3.3 Data output in Excel
Data output in Excel is very important for the solution of many problems, the main of which is to s danie reports satisfying x whole user database requests data. These types of reports are easy and understandable types of PC users. This is total " Vindualizatsiey" around the world.
To solve this problem, in many cases it is sufficient to connect ComObj and ActiveX modules
The function returns True if found OLE-object
Example
the if not IsOLEObjectInstalled ('Excel.Application') the then
ShowMessage (' Class not registered ')
else
ShowMessage (' class found ');
function IsOLEObjectInstalled (the Name: the String): boolean;
var
ClassID: TCLSID;
Rez: HRESULT;
begin
// Looking CLSID OLE- object
Rez: = CLSIDFromProgID (PWideChar (WideString (Name)), ClassID);
the if Rez = S_OK the the n // object found
The Result: = to true
else
The Result: = to false;
end;
This example searches for an active instance of Excel and makes it visible:
var
ExcelApp: Variant;
begin
try
// Looking neglect the Excel instance, if it is not found, an exception is thrown
ExcelApp: = GetActiveOleObject ('Excel.Application');
// Make it visible
ExcelApp.Visible: = to true;
except
end;
end;
You can display the data sequentially in each cell, but it slows down the work sharpen. It is better to create a variant array, and perform the assignment area (Range) of the array.
var
ExcelApp, Workbook, Range, Cell1, Cell2, ArrayData: Variant;
TemplateFile: the String;
BeginCol, BeginRow, i, j: integer;
RowCount, ColCount: integer;
begin
// Coordinates of the upper left corner of the region, which will display the data
BeginCol: = 1;
BeginRow: = 5;
// The dimensions of the array output data
RowCount: = 100;
ColCount: = 50;
// Create Excel
ExcelApp: = CreateOleObject ('Excel.Application');
// Disable Excel reaction to the events, to accelerate the withdrawal of information
ExcelApp.Application.EnableEvents: = to false;
// Create a Book (Workbook)
// If the fill pattern, then the Workbook: = ExcelApp.WorkBooks.Add (' C: \ MyTemplate.xls');
A Workbook: = Exce lApp.WorkBooks.Add;
// Create a variant array, which is filled with the output data
ArrayData: = VarArrayCreate ([1, RowCount, 1, ColCount], varVariant);
// Fill the array
for I of: = 1 to the RowCount do
for J: = 1 to ColCount do
ArrayData [ I of, J]: = J * 10 + I;
// Upper left cell of the area, which will display the data
Cell1: = WorkBook.WorkSheets [1].Cells [BeginRow, BeginCol];
// Bottom right cell of the field, which will display the data
Cell2: = WorkBook.WorkSheets [1].Cells [+ beginRow the RowCount - 1, BeginCol +
ColCount - 1];
// The area in which we output data
Range: = WorkBook.WorkSheets [1].Range [Cell1, Cell2];
// And here is the output data
// Much faster poyacheechnogo assignment
Range.Value: = ArrayData;
// Make Excel visible
ExcelApp. The Visible: = to true;
3.4 Programming mathematical processing of information in the database
Mathematical calculations by explanations.
3.4.1 Programmable mathematical quantities
The average value of
During this operation, carried out various calculation of average values in the fields of intensive and extensive infestation of parasites.This opertsii nebhodimo to learn more about the repose of data.
3.4.1.1 The arithmetic mean value
The M - arithmetic mean value - the sum of characteristic values for all objects together, divided by the total number of objects, ie, the arithmetic mean value of the trait is the quantity Formula 3.1 of mean value:
М= 
For example, if the age values in the aggregate (group) of 5 people are 30, 35, 30, 40 and 30 years, must be added to calculate the average age and the five values received amount (165) divided by five.
3.4.1.2 The coefficient of variation
If some set of the coefficient of variation does not exceed 30%, this collection is homogeneous for a given characteristic.
If the coefficient of variation exceeds 50%, the set is non-uniform. This aggregate is divided into more homogeneous parts.
If the coefficient of variation in the range of 30-50%, the homogeneity of the decision is made by the researcher.
scattering measures
- All dispersion measures (standard deviation, variance and coefficient of variation) can be computed for quantitative characteristics only.
- The value of the standard deviation and variance change when you change the units feature and the value of the coefficient of variation - does not change.
- The coefficient of variation can exceed 100%.
scattering measures
- All measures scattering shows how the characteristic value greatly varies (or rather - its deviation from the mean) in the population.
- The smaller value of the spread measures, the closer the feature values for all the objects to its mean value, and thus to each other.
- If the value of the spread action is zero, the characteristic values are the same for all objects.
The coefficient of variation is calculated using the formula(3.2):
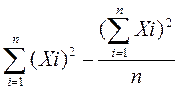
CV=
Its meaning lies in the fact that he, in contrast to the standard deviation, does not measure the absolute andrelative measure of spread of characteristic values in the statistical population.
The coefficient of variation
- Comparison of distributions based on the attributes of characteristics such as the mean and standard deviation, it is difficult in many cases, such as when these attributes are measured in different units.
- Even if the signs and have the same meaning, a direct comparison is only possible for the arithmetic value, but not for standard deviations.
The coefficient of variation
- For example, in one group standard deviation of income is 400 rubles, and in the second -. 2000 rubles, ie 5 times more than in the first..
- It can be concluded that the first group is much more uniform in magnitude revenue than the second.
The coefficient of variation
- If we consider that the average income in the first group - 800 rubles, and in the second -.. 8000 rubles, then we find that in the first group V = 50%, and in the second V = 25%, ie in relative terms is just the second group is much more uniform.
3.4.2 Standard deviation
- The most frequently used mean square (or standard) deviation s.
- The magnitude of this deviation is given by: (Formula3.3)
σ = 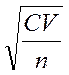
Standard deviation:
- The standard deviation is measured as the arithmetic mean, in the same units as the initial sign of itself.
- If all the sign change several times in the same way and a standard deviation change, however, if all the attribute value to increase (decrease) by a certain value, its standard deviation does not change.
(RMS) deviation.
3.4.3 error.
The error is calculated as follows:
.
3.4.4 Accuracy.
The error is calculated as follows (formula 3.4):
m= σ
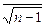
Reliability.
Reliability is calculated using the formula (3.5):
t= 
The presence of such additional information as the reliability, allowing consumers to make more informed decisions when performingpractical tasks.
The concepts of reliability and accuracy of the content are fairly close to each other. However, there are some meaningful differences.Reliability refers to the correctness or undistorted estimated magnitude of value. A reliable estimate - is first and foremost objective evaluation, unbiased and fair, made in accordance with the requirements of the code of ethics of the appraiser.
Precision implies observance of the requirements of reliability, but also characterizes objectively possible degree of approximation of the estimated value of the object to its true value. When people talk about the accuracy of the estimate, the mean reliability of the results. It is achieved by means of the applied methodological tools and taking into account the completeness of the information used. It is assumed that the independent evaluation of the principle of fully implemented, and the evaluator has the necessary professional level. Each evaluator is well aware, when the object it is possible to estimate accurately, but when - approximately.
Even an experienced appraiser is not immune from mistakes. The thing is, he was wrong on purpose or by accident. And deliberate mistake - this is not an error, and distortion. Now these two concepts - " error" and " distortion" - have legal recognition, they are fixed in the Tax Code (Part One). If the distortion of evidence of the unreliability of the error - an error.
Of course, it is difficult to discern where you make a mistake, and where - the distortion. It is considered so that any minor deviations from the true value falling within the " tolerances" - a random error. But large deviations are perceived as distortion or invalid error. A certain indication of " trust boundary" is contained in article 40 of the Tax Code. It states that the tax authorities are entitled to verify the correctness of the prices used in transactions at a deviation of more than 20 percent in either direction from the level of prices for identical (homogeneous) goods within a short period of time.
Error (error deviation) represents the difference between the estimated and the true value of the quantities. Since the value is predicted probable price that better match the appraised value of the actual price of subsequent sale, the higher the accuracy of the estimate. However, the actual price can not unconditionally accept as true the cost, as the real conditions of the transaction may deviate significantly from those of the most common conditions that meant evaluator, assessing. Nevertheless, part of the match results of evaluations with actual prices is an indicator of the success of the appraiser.
Furthermore, the criteria described above intended to apply to a normal probability distribution. It is, in fact, widely used in the analysis of financial transactions risks as its most important properties (symmetric distribution relative to the average, a negligible probability of large deviations of a random variable from the center of its distribution, the three sigma rule) can greatly simplify the analysis. However, not all financial transactions involve a normal distribution of income (distribution of select topics in more detail below), for example, the distribution of income probabilities on derivative financial instruments (options and futures) are often characterized by asymmetry (slant) with respect to the expectation of a random variable
3.5.1 Code calculating average values
z: = 0; j: = 0;
ev1: = 0; r: = 0; m: = 0;
try
datamodule2.ADOQuery1.First;
for i: = 1 datamodule2.ADOQuery1 to. the RecordCount do
begin
inc (j);
z: = z + datamodule2.ADOQuery1DSDesigner8.AsVariant;
ev1: = ev1 + sqr (datamodule2.ADOQuery1DSDesigner8.AsVariant);
datamodule2.ADOQuery1.Next;
end;
ev2: = sqr (z);
z: = z / j; M2: = Format ('% 8.0f', [z]);
c: = ev1- (ev2 / j); c2: = Format ('% 8.1f', [c]);
r: = sqrt (c / (j-1)); r2: = Format ('% 8.2f', [r]);
m: = r / sqrt (j-1); mm2: = Format ('% 8.1f', [m]);
t: = z / m; t2: = Format ('% 8.1f', [t]);
//memo1.Lines.Add('M = '+ M2 +' C = '+ c2 +' r = '+ r2 +' m = '+ mm2 +' t = '+ t2);
except
M2: = '0'; c2: = '0'; r2: = '0'; mm2: = '0'; t2: = '0';
end;
4. PROTECTING PROGRAMS FROM UNAUTHORIASED ACCESS
It needs protection from stealing information.
4.1 Protection programs written in OOP Delphi 7
Consider some of the subtleties of protection organization at a fairly popular example - suggest that the program is protected by certain code (serial number, a password), which shall be communicated to the user after the observance of certain conditions. Before registering in the program blocked any number of useful features, use annoying ads or limited work lines. After entering this code made his test and a positive outcome of test program begins to work normally.
The modern attacker has at its disposal a set of different tools to crack. They may be divided into several categories:
- Debuggers. Allow to interrupt the execution of the program when the predetermined conditions, to produce a step by step program execution, modify the contents of memory and registers, etc.. The most popular, convenient and powerful is the SoftICE debugger, which is sufficiently primitive interface has decent features and a very stable work.
- Disassemblers. Produce disassemble the program to further explore the generated code. One of the most popular - IDA. From disassembler easy enough to protect - encrypt or archive program. Then disassemble the only archiver or encoder.
- Monitoring tools. This is a set of tools that monitor file operations, registry, and network ports.
- Means of passive analysis program. They show a variety of information about the program - recoverable resources indicate communication libraries. A classic example - utility DEPENDS.EXE comes with Visual Studio. It shows what libraries used by the program and which features are imported.
- Other utilities. Their great variety (can be found on the disc like " All for a hacker", and in abundance). This variety of editors, analyzers,...
The most popular are the following monitoring programs:
The FileMon - utility that allows you to monitor all file operations. Has a convenient filter could save the report to a file. Therefore there is no point in making " secret" files somewhere in the Windows / System - their elementary find.
The RegMon - analogue FileMon, is only being monitored all the operations with the registry. Similarly, the files in the registry to create a pointless " secret" keys - they immediately catch the eye.
PortMon - monitoring of I / O ports
TCP_VIEW - monitor connections on TCP-IP
RegUtils - a set of tools to monitor the registry - makes copies of the registry, allows you to compare a copy and see the changes.
FileMon type tools can dramatically simplify the hacking program - easy to determine the place in which the program refers to the specified file or registry key.
Fundamentals of Protection - step by step
How to enter the registration code entry password or serial number is the responsibility of all - the hacker will try to catch the memory address, which will be recorded password. Then, on an appeal to this address put breakpoint (BPM team SoftICE), allowing you to catch the beginning of the registration code verification procedures. If I used the standard Windows input elements, the hacker action algorithm can be formalized, and it looks something like this:
- Set a breakpoint in the reading of the text from standard input element (GetWindowText function, GetGlgItemText KERNEL32 module)
-When you call this function, analyzing its parameters and thus determine what address will be posted, and the reading is set to appeal this memory breakpoint. And the reliability of a particular address is easy to see - after the function is introduced there will be a string
-When triggered, this breakpoint, the developer gets to the analyzer input value and a generator make registration keys or break test procedure. And then, and another is very simple to make - enough only to study the assembler and API
Consider a few solutions that can make it difficult to hack at this stage.
-Try as little as possible to use standard functions (especially the API-shnye) and VCL components. So Assembler, Assembler and Assembler more time...
The essence of this Board is obvious hope - advanced disassemblers able to recognize standard procedures of high-level languages and API - altogether different story - the SoftICE has an amazing opportunity - to load the symbolic names for all these libraries (especially for KERNEL32.DLL) - debugging is greatly simplified because we see the names of called functions and can set a breakpoint on the function call on their behalf.
- Use a non-standard method of entering a password.
The easiest way - to write the visual component to enter a registration code. He certainly would handle events from the keyboard, but the moment of reading the code can not catch the hackneyed methods. This is something, but there is a second way of hacking, based on the search for the code entered in the memory. To do this, SoftICE is a comfortable command " S start address length L 'pattern' ', which allows you to find the entered value in the memory.
- Do not store the code entered in one place!
- Do not store the code entered in plain text!
So, what should be done. First we need to make in the program 5-10 variables of type STRING and after entering the code to copy the value entered into them. Doing this will not only better in one place and to distribute the program. Thus, the search will give a bunch of addresses that will be entered code. In this case, it is necessary Postup it so - the timer will build five new string variable on the heap to writein her code. Then, at the next timer tick will build five new variable census amb in her code, and trying to destroy it. At a certain skill, you can sweep the memory values entered code and to search almost useless. And such copying can be combined with verification code or emulation of the test. Then, these lines do good any operations - to compare with anything...
Paragraphs 4 and 2 can be combined - to create a component that will allow to enter the code non-standard way, with its simultaneous encryption of.
Analysis of the registration code. So, the code is entered and taken steps to ensure that it was not easy to find (although it can be found, but this time, skill...). Now the next step - the analysis. So advice immediately:
-In no case did not analyze the code as soon as you enter it.
The code further analysis of its input, the better. The most reasonable - after entering the code to thank the user for their cooperation and to inform you that the program registration will be made in due course. A code analysis to produce, for example, 1-2 minutes in a completely different place in the program.
- Do not test the code in one place and do not write to test the function.
It suffices to find and disable this check, and protection compromised. If several tests, they are different and distributed under the program, the hacking difficult.
- Do not check the password one algorithm.
It is recommended to develop 2-3 test algorithm, such as 1-2 digits must be divisible by 3, and 3-7 imposed on any algorithm on the user name must be given in the amount of 4. These two checks are carried out at various locations with a large enough temporal spacing - cracking the first method a hacker will not speculate on the existence of a few that will emerge over time.
- In no case did not take any action after the review. For some unknown reason, most of the programs look like this
IF NOT (SuperRegCodeCheck) then
Begin
ShowMessage ('Invalid code, can no longer operate ");
halt;
end;
In the example code for some routine checks and a mismatch is taking active steps. Nai best move - wait for the day are two.Moreover, all actions of inspection should include as far as possible by issuing messages and other actions to be taken upon detection of an incorrect code.
- A red herring.
In addition to the actual function code review very nice to make a couple of sham - they will be called upon to enter a code, carry out active manipulation with the entered value, to issue reports on the code entered is incorrect... - ie, divert attention from the real review.
- Do not store the test results in a variable and use it to explicitly limit the functions of the unregistered program.
A classic example of violation of this rule
The NOT the IF (LegalCopy) the then
ShowMessage ('Saving works only in the registered version')
else
SaveFile;
Thus elementary analysis shows that the variable stores the result LegalCopy check and putting it breakpoint can catch the very test.After editing the values in the memory, you can temporarily make a copy of " registered", and setting breakpoints to change this variable will display in place of its validation. And hacking is to ensure that the function verification code is truncated to two assembly instructions:
MOV [ address LegalCopy], 1
RET
- (Derived from 9) Do not store the results on the disk check, or in the registry.
A typical error - found that the copy is registered and made a mark somewhere. Catch is simply (see. REGMON description and FILEMON). The best way - to save your password and user name in the form in which it brought them. Then, every time you run the program to check the correctness of the code, but not forgetting the Council _11. Do not check immediately when you start an application or immediately after reading the stored name or code. Remember that reading the code and enter it in the registration window identical protection measures - duplication in different areas of memory encryption.
General tips for protection programs
-CRC - checksums. Every file data block or string can be protected checksum, which can then be calculated and compared with a standard. In comparison with the standard course should be conducted with care - see the first 11 councils.. Thus, the Board 12. Protect your programs and data checksums. This will help not only against burglary, but also to protect the program from a virus or Trojan implementation.
- Use encryption software and data. Very good compression program and data. And change their problematic - will have to let go, edit and compress.
- Capture incremental debugging. There are many ways. The easiest and most reliable way - timer. When the program periodically fix the system time and look forward to the work pieces of code between them. And if 200-400 processor commands work for 2-3 minutes, then there is something to ponder.
- Do not define the date and time standard way!! Come up with something original.
-Not should keep anything secret in the files or the registry. Working with files or registry can be logged and analyzed in detail, and every secret will be revealed.
-Not store anything important in plain text, particularly messages such as " It's unregistered version...", " The password you entered is incorrect...".
Create labels for the organization of time limit
Protection " limit work time" is that the program is how to fix the time of its first launch and running a set time (usually 20-30 days).After the expiration of this period, the program refuses to run. The trick in another - how to fix your computer date of the first run (of course so that the annihilation of the program and its re-installation does not give effect). The use of " secret" file system folders, or changes to existing files easy to catch using FILEMON. Register of the same is no longer due REGMON. Other methods (such as entries in the BOOT sector...) is also unacceptable - not a time for Windows, all this does not take place. The most original (in my opinion) to flash the date into the program itself and constantly update it on your website (of course, automatically). Thus the count implicitly comes from the time of downloading the program from the website. Is there truth and negative - this program can re-download after the deadline and get 15-20 days.... On the other hand it is original - the user will sooner or later get tired of downloading this program and he or abandon it, or buy it. But it is worth remembering that the program can be downloaded multiple times and compare the options, identifying where the date is. So you should make sure to change almost all of the file (for example, change a couple of compiler options)
For tips on making registration codes
Formation of codes can be carried out in the following areas:
- Firmly fixed codes stitched into the program. They are usually a little publicity and brings protection to zero.
- A certain code verification algorithm. A little better than the first, but only slightly. Take for example Windows code - knows anyone
- code verification algorithm using the user name. It is obvious that for each name is a unique number (or numbers - there may be several, depending on the algorithm). This is better, but the illegal distribution rests on selfishness registered users - nothing prevents them to betray the name / password public, but then at least we can calculate the culprit and block code
- code verification algorithm using the user name and some of the unique and dynamically changing parameters, such as information about the computer. It is reliable, provides a binding to the computer, but in this age of constant upgrades is very inconvenient.
-On-Line Registration. It consists in the fact that in the On-Line program binds to the site developer (or a company engaged in software produzhu) and sends back user revizity. In response, the program is transferred to the registration information. This method can be and is good for a number of programs.
-No one can guarantee that will give specific program in the Internet. And it can pass anything you want - PC settings, passwords, any data, etc.
- The specific user nozhet not have access to the 'Net. This is especially true for programs whose work is not directly related to the Net. And his record this program almost no one to your computer will not start up (for reasons of items:
1) Protectors.
Protector are programs designed to protect software against hacking. Currently on the market are a lot of tread, but almost all have one drawback - they do not modify the source code (protection software is a common package of the entire file, with the " protected" self extractor, which eventually decompresses the file). After the end of unpacker program can simply " sdampit" and in the end without too much difficulty to get the source (unpacked) file. Hackers developed many tools for the automatic removal of the most popular protectors.
4.2 Protection against hacking and Access databases
Under the " protection of the database" is defined here as a way to prevent unauthorized access to information stored in tables.Protection of the source code of forms and modules not considered.
The relevance of this topic is extremely high. This can be seen in the first place in the ranking (18 thousand downloads) article " Protecting the mdb database " which was written by Yuri Sherman.
This method of protection allows you to set a password to open the database for all users. To create the database you need to open the file in " exclusive" mode, and select Tools / Security / Set database password. To work with a database in MS Access to enter the password.Here is an example of working with the database file using DAO and ADO.
Public Sub TestDAO()
theDim MWS ofAs DAO.Workspace
theDim mdb ofAs DAO.Database
theSet MWS = DBEngine.Workspaces(0)
theSet mdb = mWS.OpenDatabase _
('the C: \ a97.mdb ", True The, True The, "; the pwd = 123 ")
End Sub
Public Sub TestADO()
theDim CnDB ofAs New ADODB.Connection
CnDB.Open " Provider=Microsoft.Jet.OLEDB.4.0" & _
"; The Data the Source = the C: \ a97.mdb" & _
"; The Jet the OLEDB: the Database the Password = 123"
End Sub
This is not the most reliable way to protect databases. There is a sufficient number of free and paid tools that display the password.Including available source code in VB allows you to read a password. In other matters not so bad.
This method allows us to introduce an additional layer of restrictions related to the DB Access work. Based on the creation of the file of the working groups, which are determined by the user names, passwords, and the right to work with different database objects.
Steps to create a secure file:
- Create a new workgroup file.
- To do this, 97-2000 Access WRKGADM.EXE run the program and select the menu item in 2003. Access " Service / Security / Workgroup Administrator." The Administrator Hit " Create" button, specify the name, organization and group code. Specify the name and location of the file to be created. For example:
- Name: test_Name
- Organization:
code This pabochey groupes: ctpochka 20 cimvolov.
- Fayl pabochey gpyppy: C: \ test \ gr.mdw
- To create a shortcut to run the ms Access using established mdw file. The label must contain the following line: [path to MSACCESS.EXE] / WrkGrp [path to mdw file]. For example: " C: \ Program Files \ MSOffice2003 \ OFFICE11 \ MSACCESS.EXE" / WrkGrp C: \ test \ gr.mdw
- Running Access c Using this shortcut you need to open the menu item " Service / Security / Users and Groups". In the dialog box, you must create a new user and add it to the group " Admins". For example, " test_Polzovatel" with " 987654321" code was created
- Now you need to open Access on behalf of the created user. To this must be added to the shortcut string: / user [user name].
- Start Access c using this shortcut. Now create the user must be assigned a password. This is done in the same dialog, " Users and Groups". Suppose the user " test_Polzovatel" assigned password " test_Parol". Next, you must create a new database. At the same time the owner of the database, as well as all created or imported objects (tables, queries itp) is a user whose name is indicated in the label.
- Once the database is created, it is desirable to remove the " Admin" from the group " Admins", and select the group " Users" rights to database objects and to open a database.
- Adding to the label name a secure database.
For example:
" C: \ Program Files \ MSOffice2003 \ OFFICE11 \ MSACCESS.EXE" C: \ test \ db2k_test.mdb / WrkGrp C: \ test \ gr.mdw / User test_Polzovatel / pwd test_Parol
Here is an example of opening a secure database at the user level via DAO and ADO
Public Sub TestDAO()
theDim MWS ofAs DAO.Workspace
theDim mdb ofAs DAO.Database
DBEngine.SystemDB = " TheC: \test\gr.mdw"
theSet MWS = DBEngine.CreateWorkspace _
(" ", " test_ User ", " test_ Password ", dbUseJet)
theSet mdb = mWS.OpenDatabase _
(" theC: \test\a97.mdb", TrueThe)
End Sub
Public Sub TestADO()
theDim CnDB ofAs New ADODB.Connection
CnDB.Open " Provider=Microsoft.Jet.OLEDB.4.0; " & _
" The Data the Source = the C: \ test \ a97.mdb; " & _
" The Jet the OLEDB: the System the database = the C: \ test \ gr.mdw; " & _
" TheUser ID=test_ user; " & _
" Test_thePassword= Password; "
End Sub
Removal of such protection.
Create a new database. The label set the path to this database, MDW file protected database name and owner password. Open with that label a new database. Import it in the table of the protected, then change for all database objects the owner to Admin. To find out the name and password of the database owner can use specialized programs described in the review of Access Passwords. In the absence of working groups of the file can be recovered. To do this, you need to know the names and IDs of owners of database objects. This information is contained in the database file and can be retrieved with the help of programs such as AOPR. Using this data creates a new file. (sequence described above)
It is not necessary to use the program to help you determine your password database or user. Most programmers do not care about hiding the password in the program. Running the program running with a secure database is necessary to open in the hexadecimal editor WinHex virtual memory of the application. After a search Unicode strings 'User ID ='; 'Password ='; 'Database Password =' or 'pwd =' You can find the user name, password, and database password.
You can completely ignore the existence of protection. To do this, use AccessRecovery, which creates a new file without protection and transfers it tables, queries, forms, macros, reports and code modules.
Suffice a simple way to mislead - to change the database file extension. Seeing an unfamiliar extension, not everyone will try to clarify the nature of the file. In addition, it is possible to associate the extension with your program, so that when you click on the file gets your application, not Access. It is advisable to open a file with exclusive access, as in this case will not be created ldb file.
First, this method is aimed at countering the definition passwords using special programs. The method is based on the fact that the password database Access 2000 format and 2002-2003 - a text string in Unicode format. At the same time, there are no restrictions on its content. The standard way to install and use the database password, it means the keyboard input in the dialog box. If the password contains Photo unprintable characters, they will not be correctly displayed the program opens the database passwords. On the other hand, this password can not be entered in the dialog box when opening a database MS Access.
The fact that in the specification database and for DAO 3.60 certificate specified that the maximum number of characters in a password - 14. But in fact there may be 20. In this case himself Access 97 does not allow a password strings longer than 14 characters. In Access 2003, the specification also said about 14 characters, but the program allows the entry of 20. It is also possible to use a non-printing characters, which causes most of the programs hacking passwords to a screeching halt.
To set this password is required to use the program that uses the CompactDatabase method of the DAO or ADOX libraries.
Burglary protection.
- Firstly, you can use AccessRecovery.
- Second, we can try to determine the password database with the help of special programs. In a review of Access Passwords is a summary table of their capabilities.
-Third, you can find the password by analyzing the code of the program in the debugger. Whatever the password, he still passed as a text string in the method of opening the database. If you have a certain experience -. It is not a very difficult task P Arola might find using OllyDbg debugger, finding the place create ADODB.Connection
- Check or change the database password, you can, without the aid of special programs. In Access 97, is obtained by adding a password to XOR the password with 20 byte sequence. The values of these bytes can be obtained from any non-password-protected mdb file.Starting with Access 2k, in connection with the use of Unicode, for storing the password 20 characters set aside 40 bytes. When encryption is also used for adding XOR, but to obtain a sequence of bytes corresponding to a blank password, create a file with the date of the test database. These bytes can be entered into the test file and reset your password, or add them with the same bytes of the test file and get the password value.
In this paper does not address the possible manipulation of the files of the working groups. Surely there are ways to protect the stored passwords from them too interesting programs, but it loses its meaning when used AccessRecovery, that protection does not notice it.
protection method is based on a modification of the first byte of the file. Thus, before the opening of the database file is stored in its correct title, stored in the program, and after the closing of returns is incorrect. When you try to open a database file using ms Access, you receive an error message. Not a bad way to combine this with the change of the file extension. For example, we can take the title dbf file and burn it to the top of mdb file. Next, change the file extension to dbf and enjoy the result. Database can now be opened in Excel, Access or any other program that allows to read dbf files. here is example this conversion:
' Modification of the header file database
'Ex: Call BaseProtect (" C: \ 01.mdb", True)
Public Sub BaseProtect (the sPath of As the String, BLOCK of As BooleanA)
theDim iFn ofAs anInteger
iFn = FreeFile()
the Open the sPath For The Binary the Access the Write of As #iFn
thePut #iFn, 5, theCStr(theIIf(BLOCK, _
" ProtectDataBase", " of Standard the Jet the DB"))
Close #iFn
End Sub
The method is not sufficiently effective as a program that works with the database, you can interrupt and will not artificially protected database on a disk. Therefore, it should be used only in combination with other methods.
This method - the further development of the file header modification ideas to counter program, reading passwords. The method is based on the fact that for a DB Access 97 and 2k programs use different algorithms for reading the password and thus attempt to determine the version of mdb file.
To determine the version can use a sequence of 40 bytes starting from the beginning of the file 122. If the DB Access 97 to enter this sequence of Access 2k, then we get an interesting result. Program ms Access, ADO and DAO normally work with this file, but the majority of hacking programs passwords fall for this trick. A similar result can be obtained by transplanting a byte sequence from Access 97 to Access2k header File Access 2k shown in table 4.1 green fragment recovered password database.
blue - a fragment characteristic of the database version.
Table 4.1 - The best protection against hacking problems
Offset 0 1 2 3 4 5 6 7 8 9 A B C D E F
00000000 00 01 00 00 53 74 61 6E 64 61 72 64 20 4A 65 74
00000010 20 44 42 00 01 00 00 00 B5 6E 03 62 60 09 C2 55
00000020 E9 A9 67 72 40 3F 00 9C 7E 9F 90 FF 85 9A 31 C5
00000030 79 BA ED 30 BC DF CC 9D 63 D9 E4 C3 9F 46 FB 8A
00000040 BC 4E 9B 6D EC 37 40 D2 9C FA DB C8 28 E6 0E 20
00000050 8A 60 49 02 7B 36 E8 E4 DF B1 6A 62 13 43 D2 39
00000060 B1 33 29 F7 79 5B 8F 23 7C 2A 4F E9 7C 99 08 1F
00000070 98 FD DC 75 0C FF D8 FD 82 66 5F 95 F8 D0 89 24
00000080 85 67 C6 1F 27 44 D2 EE CF 65 ED FF 07 C7 46 A1
00000090 78 16 0C ED E9 2D 62 D4 54 06 00 00 34 2E 30 00
|
|